Simulated phishing exercise
Posted on Tuesday 6 August 2024
This email told you that there had been a suspicious sign-in attempt to your University Google account, and asked you to sign in with your username and password to review your account details and update your password.
52 people clicked on the link (15 percent of recipients) in the email and ten people entered their details into the fake Google login page.
Those people who did enter their account details were then taken to a page reassuring them that this was just a simulation and explaining why the original email was suspicious. No passwords or usernames were accessed or stored.
Why did we do this?
Phishing emails are a serious threat. Once a cybercriminal has your username and password, they could then try to access our university systems to steal or corrupt our information, or impersonate university staff.
Much like a fire drill, running phishing exercises such as this reminds us of this threat and how easy it can be to fall for fake emails. We can then use this as an opportunity to refresh our knowledge of how to spot phishing emails.
The email
Here is a copy of the email with the signs it was a phishing attempt indicated by red circles (there were variations on country, city and IP address listed).
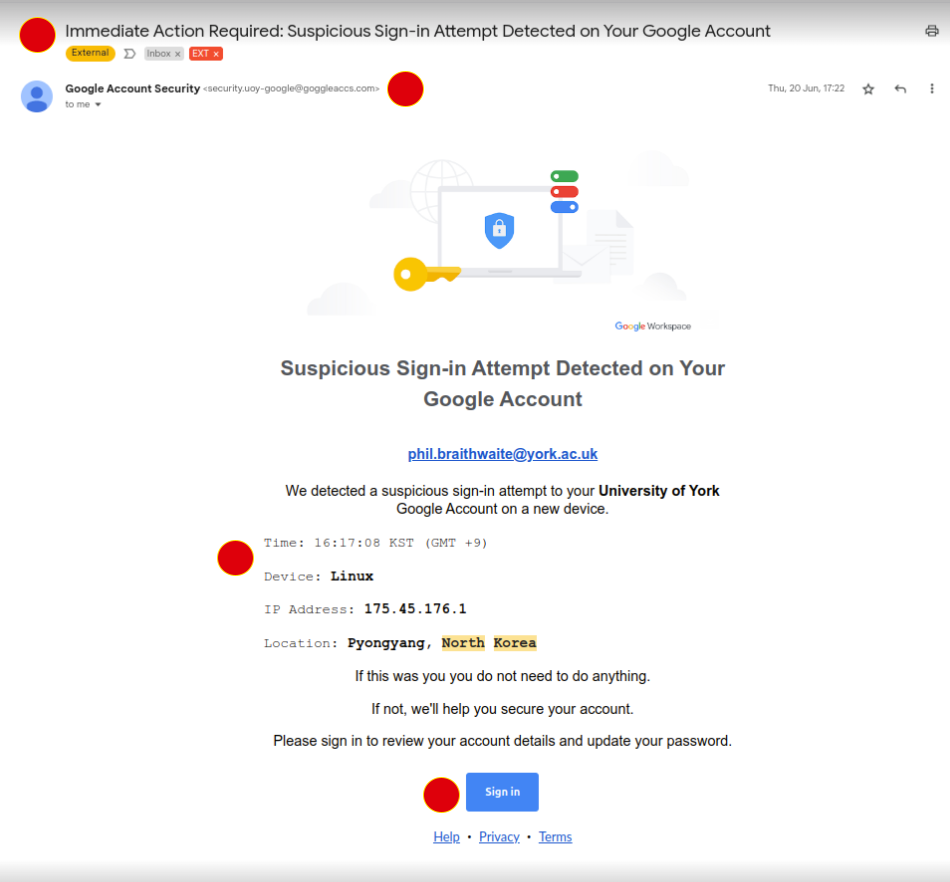
Screenshot of the phishing email with the subject heading 'Immediate Action Required: Suspicious Sign-In Attempt Detected on Your Google Account.'
- A sense of urgency: always be suspicious of emails which play on your emotions to provoke an immediate response.
- Sender's address: check that this address matches the domain of the proposed sender. If a seemingly trustworthy site emails you (such as Google), visit their site and login there rather than through the email.
- Information dump: be wary of any emails which try to confuse or alarm you with lots of extra information or technical terms.
- Hyperlinks: cyber criminals can use these links to hide malicious websites. Hover over the URL with your cursor to see where the link is taking you.
If you think an email is phishing, report it to your email provider. If you’re not sure or think a phishing attempt is particularly convincing and could trick other people at the University, please let IT Services know.
Read our full guide to identifying suspicious and phishing emails.
