Important information: Duo phishing scam
Posted on Thursday 2 May 2024
The email claims to come from the organisation’s HR department and includes a link which, if opened, brings up a login page and asks recipients to enter their username, password and complete two-factor authentication to receive a one-time passcode (OTP). The phisher then uses this code and the username and password provided to add a device to the user's 2FA account.
This means the phisher can authenticate and access services and applications which use 2FA either directly or via our Virtual Private Network (VPN).
The main two-factor authentication service used at York is Duo. You must only approve Duo notifications which you have requested yourself.
What we're doing
To protect ourselves against such an attack happening at York, we are making a number of changes to Duo over the coming weeks.
Device registration- imminent
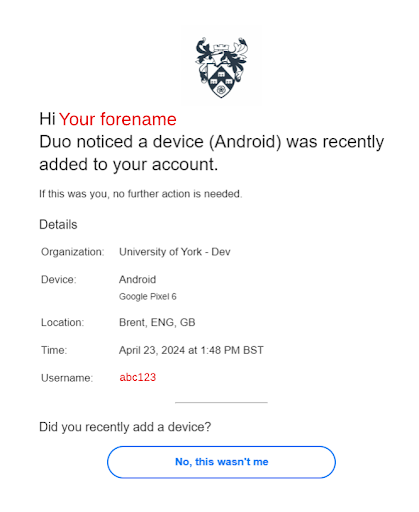
When you add a new device to your Duo account, you will receive an email from no-reply@duosecurity confirming this. Please check this email to make sure the device details are correct. If you did not add a new device account to your account, select the ‘no this wasn’t me’ option and forward the email to itsupport@york.ac.uk.
A copy of what this email will look like can be found below. To make sure the email is genuine and not a different phishing attempt, check that the sender's address is no-reply@duosecurity. Note that the genuine email will be personalised to you and include your name and username.
Duo app notifications- imminent
When you register a new device with Duo, you will receive a notification in the Duo app. If this was not initiated by you click the ‘No’ option presented.
Changes to one-time passcodes
In June we will be moving to a new version of Duo. As part of this new version, the way you receive SMS codes will change. Currently if you choose to receive Duo codes via SMS, you receive 10 codes at a time which do not expire until you use them. Once we have moved to the new version, you will receive one code at a time.
Best practice for using Duo
The best way to defend against an attack targeting 2FA is to use the Duo app to approve authentication rather than a one-time passcode, i.e. SMS codes sent to your phone or the six digit number in the Duo app on your phone. The app allows you to securely respond directly to authentication requests whereas attackers may be able to intercept one-time passcodes.
You can download the app through either Google Play Store or Apple App Store.
Using the app doesn't give the University any access to your phone. The only information made available is your mobile number and the model of your phone and this is only shared with a limited number of IT Services staff. This information is not shared beyond the Duo service.
If you have any questions about these changes please contact IT Services.
