Cybersecurity Awareness Month: simulated phishing exercise
We recently sent out a simulated phishing email to a number of staff inviting them to join a new professional network.
The email asked those who were interested to activate their account by signing in with Google or Microsoft. Of the 650 people who received the email, nobody reported it to IT Services.
If you think an email is phishing, report it to your email provider. If you’re not sure or think a phishing attempt is particularly convincing and could trick other people at the University, please let IT Services know.
Why did we do this?
Think of phishing exercises like fire drills; they help us stay prepared. A phishing email can arrive in your inbox at any time so it’s important that we regularly test our ability to spot them (we ran a similar phishing exercise in August).
Phishing emails are a serious threat. Once a cybercriminal has your username and password, they could then try to access our university systems to steal or corrupt our information, or impersonate university staff. Many members of staff at the University may be widely known externally, or have their email address publicly available, making it easy for cybercriminals to send them targeted phishing emails.
The email
Here is a copy of the email with the signs it was a phishing attempt indicated by red circles (there were variations on cities listed).
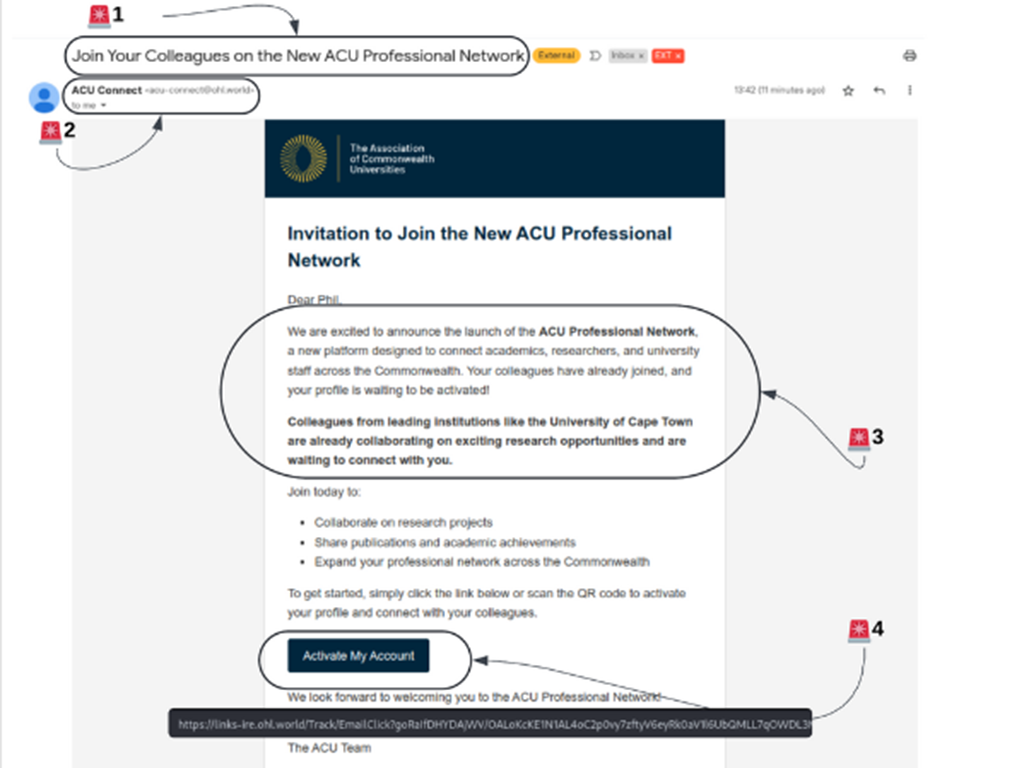
1) Unexpected messages: be cautious of unsolicited messages, even if they appear to come from legitimate organisations or your known contacts. Cybercriminals often attempt to impersonate trusted sources in order to trick you into signing up for new services or visiting unknown websites. Always verify messages, especially if they are unexpected or offering something new.
2) Senders address: if you receive an email from an organisation or person you're not familiar with, it doesn't necessarily mean it's a phishing attempt however, you should always be cautious with emails from unknown senders.
If the email appears to be from an organisation, especially one you’ve never heard of, check that the sender's email address matches the organisation's name and domain. A legitimate email address will typically (although not always) use a domain that matches the organisation's official website (e.g., @company.com).
For lesser-known or new organisations, you can:
- Search online for more information about the organisation.
- Verify the sender's email domain by checking their official website or contact information.
If the sender’s address uses a public domain (like @gmail.com or @yahoo.com), or if the domain doesn’t match the organisation’s name, it’s often a sign of phishing.
3) Social engineering: beware of emails that use techniques such as flattery or playing on the human “fear of missing out” to encourage you to click links in emails or sign up for new services. If you're ever unsure if something is phishing or a genuine marketing email, it often helps to discuss it with someone else to get a second opinion.
4) Suspicious links: hyperlinks in emails are typically disguised within buttons or text. Prior to clicking on any link, hover over it to review the URL for legitimacy. For instance, a link leading to a website like `goggleaccs.com` instead of the expected `google.com` should raise red flags as a potential phishing attempt.
Read our full guide to identifying suspicious and phishing emails.
Why do we fall for phishing?
Many people believe they’ll never fall victim to phishing emails but even the best-intentioned of us can miss certain signs, especially as phishing emails continue to become more sophisticated.
Had a stressful day and just want to clear your inbox? Under pressure to get things done by a certain time? These everyday circumstances can result in us not exercising our usual judgement and clicking on a link in an email without thinking. It’s important to remember that phishing emails are designed to mimic real emails as closely as possible to try and prompt an instinctive response. According to Psychology Today, some scammers may purposely only target impulse thinkers.
Cybercriminals employ a number of psychological tactics to trick people into sharing their information:
- Fear: messages may claim that your account will be suspended or blocked unless you reply or click on a link. They might also say that your security has already been compromised and try to create a sense or urgency so that you act quickly.
- Curiosity: phishers may try to exploit our natural curiosity by using subject lines such as “You won’t believe what we found!” or by offering exclusive offers and deals.
- Authority: often emails will claim to come from trusted organisations or individuals (such as your manager) to get you to comply.
- Social validation: phishers tap into our tendency to want to ‘do what everyone else is’ by claiming that X amount of people have already clicked on a link or used a service to make it seem legitimate.